汇编语言与逆向工程实验报告13
配置环境
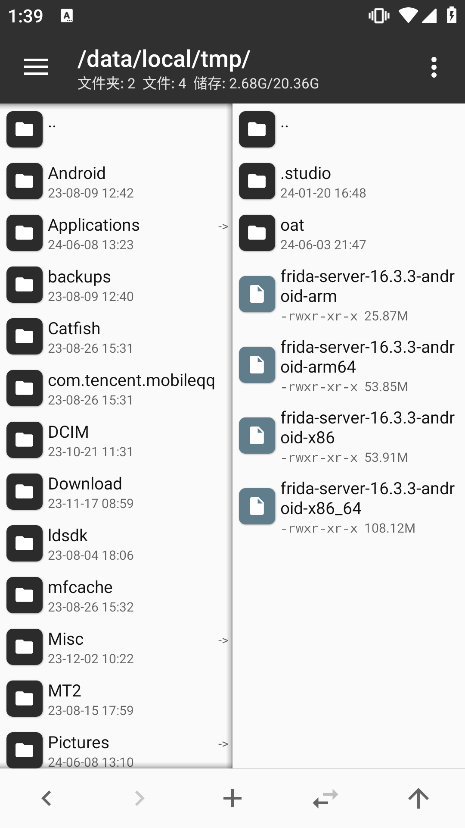
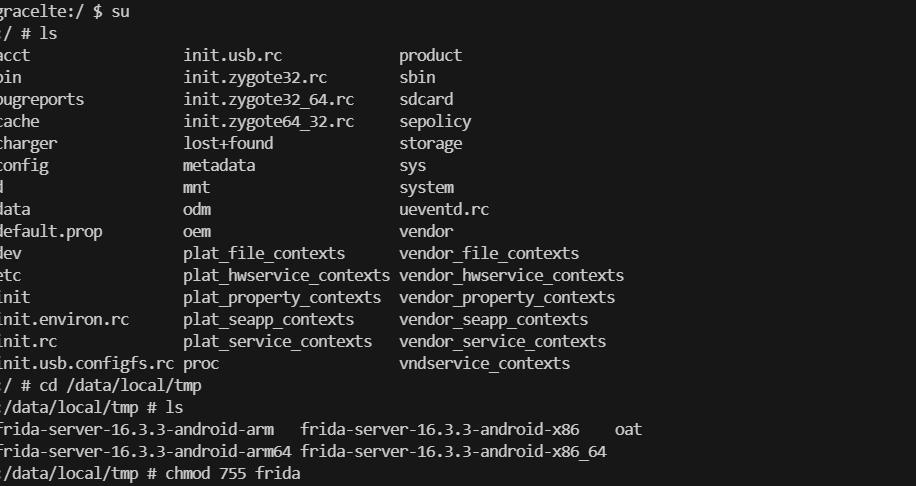
安卓模拟器上传 Frida-server

Windows 连接安卓模拟器

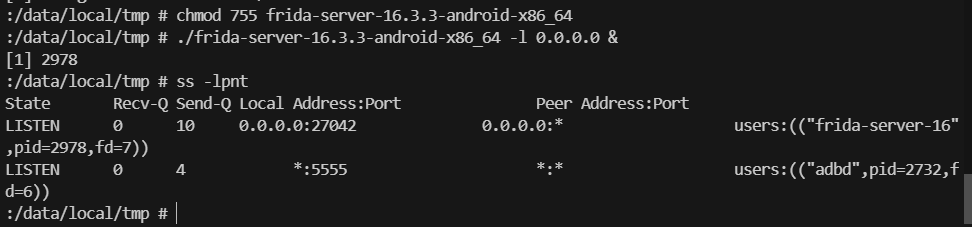
运行 Frida-server

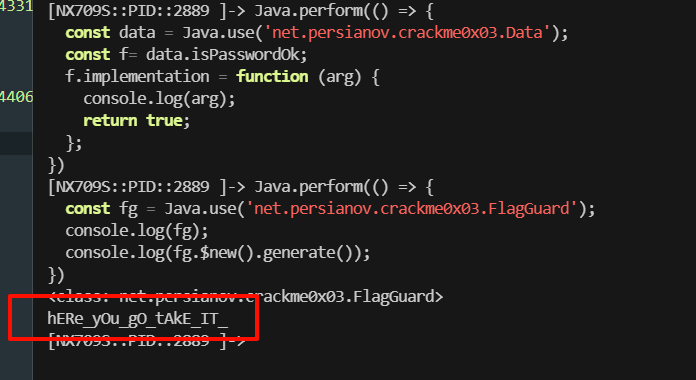
hook
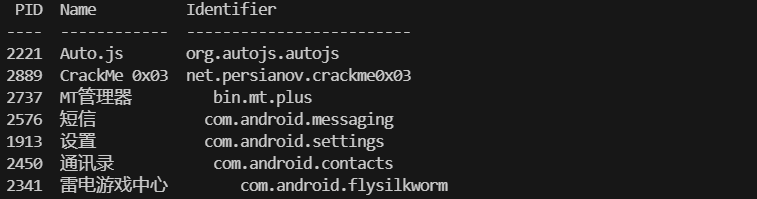
查看 PID

连接进程

hook 函数拿到 flag

exp
1 | Java.perform(() => { |
1 | Java.perform(() => { |
- 标题: 汇编语言与逆向工程实验报告13
- 作者: W1ndys
- 创建于 : 2024-06-08 13:38:14
- 更新于 : 2025-10-27 19:25:00
- 链接: https://blog.w1ndys.top/posts/a4c2b40a.html
- 版权声明: 版权所有 © W1ndys,禁止转载。
评论